Aiven supports SAML login
Customers can now include their Aiven projects in their SAML authentication workflows; find out how to implement it in the Aiven platform.
John Hammink
|RSS FeedDeveloper Advocate at Aiven
Aiven now supports SAML authentication, which streamlines account management and password policy enforcement. SAML - or Security Assertion Markup Language - enables a form of SSO (single sign-on) authentication by allowing authentication and authorization data between users and auth providers to be exchanged.
We currently support authentication using Google G-Suite and Okta, with plans to support others in the future.
As an example, instead of having to invite every user to each project individually, admins merely have to invite members to use SAML authentication once and they are automatically enrolled into every owned project. This level of access delegation is not available under plain password authentication.
Enabling SAML on Aiven
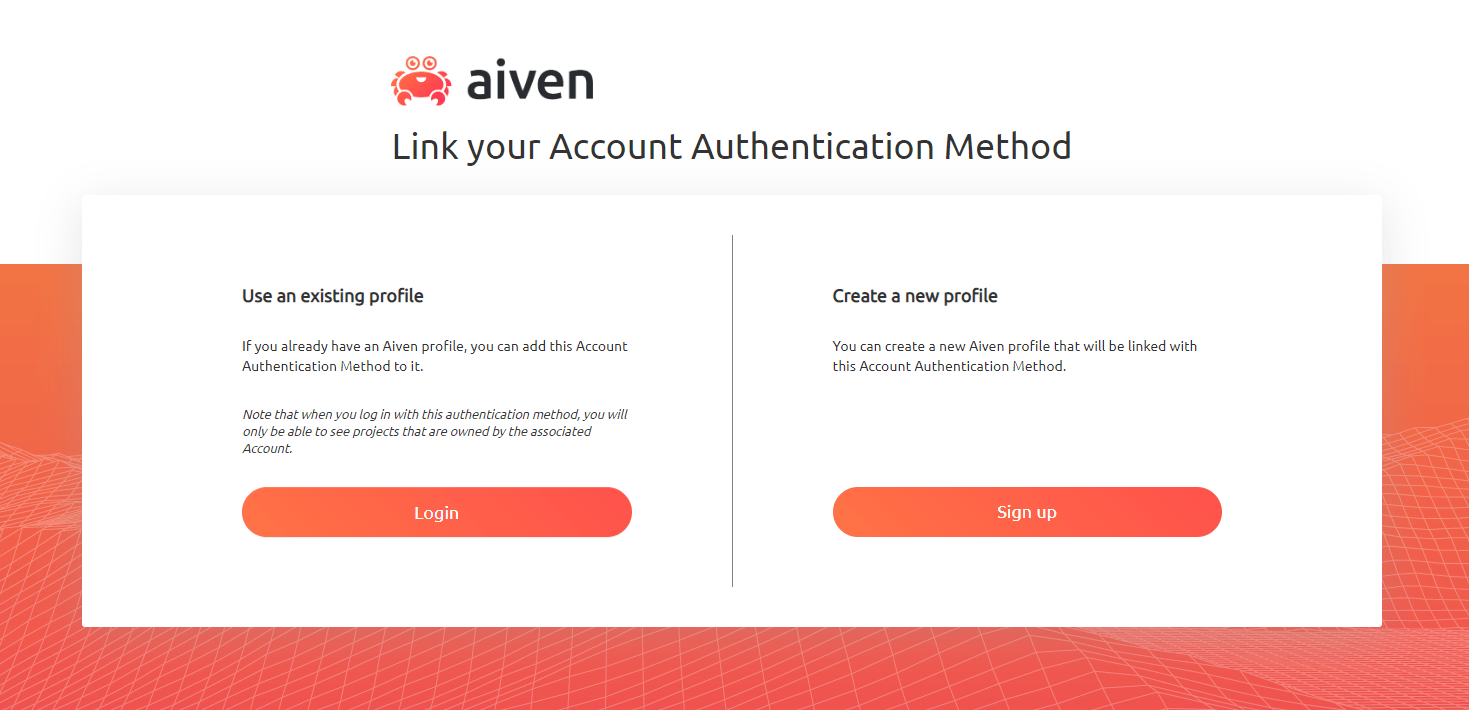
To enable SAML authentication, the admin of an Aiven account sends an invite link to their project collaborators. That link will go to an Aiven Console page where the user can choose to either link an existing Aiven profile, or create a new profile using the SAML authentication provider associated with the account.
Clicking Login will send the user to the login page and redirect to the SAML platform so that a corresponding SAML authentication method can be added to the profile. Clicking Sign up will direct the user to a page where a new auth profile for the user can be created.
Wrapping up
With SAML authentication, Aiven service admins have more options for managing user access to Aiven projects. Follow our blog, changelog RSS feeds, Twitter feed or LinkedIn page to stay current on new features.
Stay updated with Aiven
Subscribe for the latest news and insights on open source, Aiven offerings, and more.