Improving security: Aiven and GitHub's secret scanning partnership
Announcing Aiven’s partnership with GitHub's secret scanning program to protect your cloud data infrastructure
Dewan Ahmed
|RSS FeedSenior Developer Advocate
Have you ever accidentally committed a secret on GitHub and then wished you could go back in time? When you commit code to GitHub, all of the changes you make are visible to everyone who has access to that repository. Even if you unintentionally commit a secret to a repository, it can be accessed by anyone who has access to the repository. This could potentially lead to sensitive data being compromised or unauthorized actions being taken. In this blog, we’re excited to inform you about Aiven’s partnership with GitHub, customizing their secret scanning program to detect sensitive data specific to the Aiven environment.
The need for secret scanning
Committing secrets to GitHub is a common mistake, but it can have serious consequences. For example, if you commit an access key for a cloud provider, an attacker could use that key to spin up instances or access your resources. Similarly, if you commit a password to a database, an attacker could use that password to access the database and steal or modify data.
Finding and fixing security vulnerabilities in code can be time-consuming and resource-intensive. Secret scanning automates this process by scanning code for potential security risks, saving developers valuable time and resources.
Many regulatory requirements, such as PCI DSS and HIPAA, require that sensitive information be protected. Secret scanning helps ensure compliance with these regulations by identifying and preventing the exposure of sensitive information.
GitHub secret scanning - under the hood
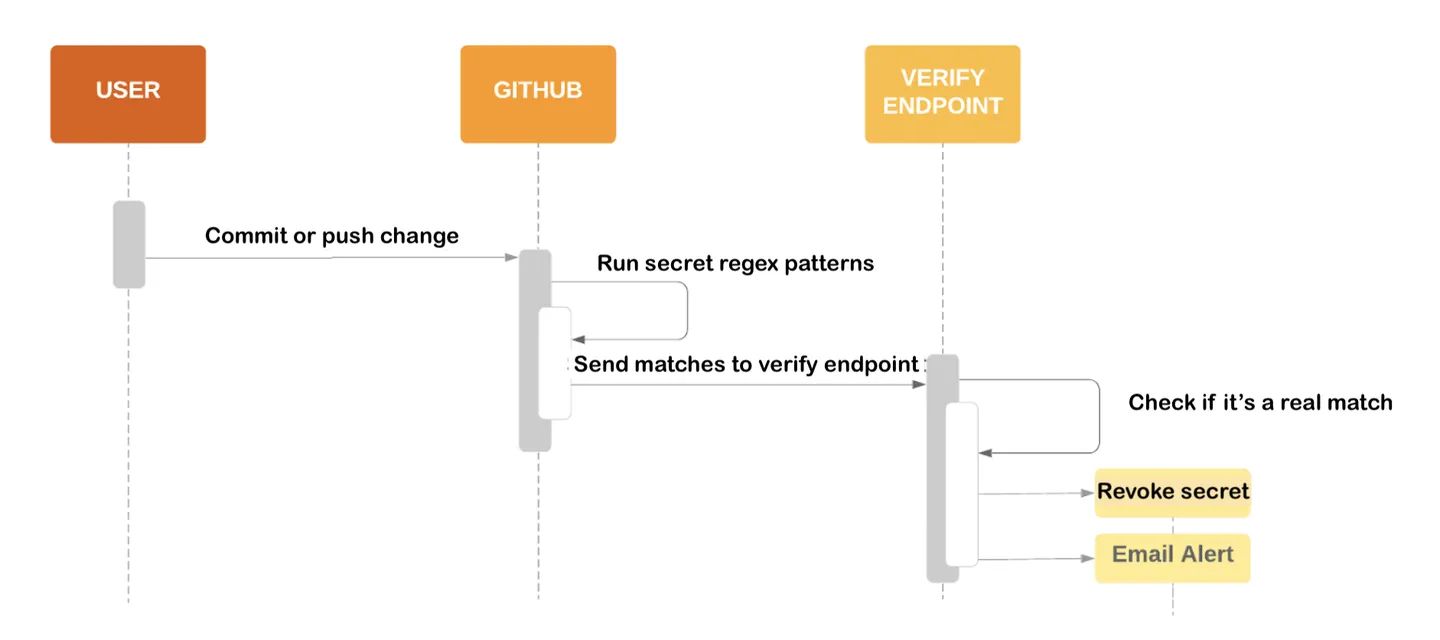
How does GitHub recognize a string as a secret? Under the hood, GitHub secret scanning uses a combination of regular expressions and machine learning to detect secrets. The regular expressions are used to scan for known patterns, while the machine learning algorithms are used to identify new patterns that may indicate a secret.
For example, the action might scan for patterns like AWS_SECRET_ACCESS_KEY or API_KEY. When a secret is detected, GitHub raises a security alert, which is visible in the repository's security tab. The security alert includes information about the file and line number where the secret was detected, as well as a suggestion for how to remediate the issue.
When a match of your secret format is found in a public source, a payload is sent to an HTTP endpoint of your choice. This endpoint can be specified by an individual or a company participating in the GitHub Secret Scanning Partner Program.
The following diagram is taken from the GitHub documentation:
Why is Aiven participating in the GitHub secret scanning partner program?
Aiven has partnered with GitHub to enable you to scan private repositories for Aiven secrets and API tokens, something that was previously only possible on public repositories. This helps you keep your confidential code as secure as your open source packages.
Private repository scanning works a little differently than public repository scanning. When a match is found in a private repository, the repository admins and committer are alerted, and those responsible can manage the issue via the Security tab in GitHub. GitHub Enterprise customers with GitHub Advanced Security enabled can also configure push protection on private repositories, which will prevent any commits containing matching secrets from being pushed to a GitHub repository belonging to that Enterprise. GitHub enabled push protection on all public repositories on 9 May 2023.
In conclusion, Aiven's partnership with GitHub on their secret scanning program is a significant step forward in helping customers keep their code and secrets safe. By informing customers if/when an Aiven token is leaked, Aiven is playing a vital role in the shared responsibility model for data infrastructure security. This proactive approach to security is essential for ensuring that sensitive information is protected and that compliance requirements are met. With Aiven and GitHub's secret scanning program, customers can feel confident that their code and secrets are safe and secure.
Further Reading
Stay updated with Aiven
Subscribe for the latest news and insights on open source, Aiven offerings, and more.